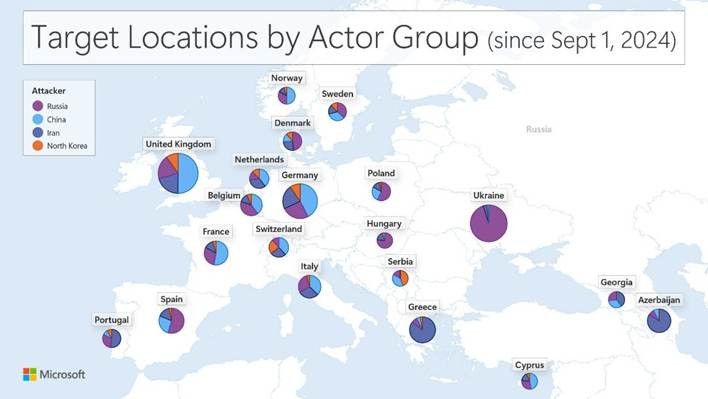
As AI and digital technologies advance, the European cyber threat landscape continues to evolve, presenting new challenges that require stronger partnerships and enhanced solutions. Ransomware groups and state-sponsored actors from Russia, China, Iran, and North Korea continue to grow in scope and sophistication, and European cyber protection cannot afford to stand still.
That is why, today, in Berlin, we are announcing a new Microsoft initiative to expand our longstanding work to help defend Europe’s cybersecurity. Implementing one of the five European Digital Commitments I shared in Brussels five weeks ago, we are launching a new European Security Program that adds to the company’s longstanding global Government Security Program.
This new program expands the geographic reach of our existing work and adds new elements that will become critical to Europe’s protection. It puts AI at the center of our work as a tool to protect traditional cybersecurity needs and strengthens our protection of digital and AI infrastructure.
We are launching the European Security Program with three new elements:
- Increasing AI-based threat intelligence sharing with European governments;
- Making additional investments to strengthen cybersecurity capacity and resilience; and
- Expanding our partnerships to disrupt cyberattacks and dismantle the networks cybercriminals use.
We are making this program available to European governments, free of charge, including all 27 European Union (EU) member states, as well as EU accession countries, members of the European Free Trade Association (EFTA), the UK, Monaco, and the Vatican.
Together, these efforts reflect Microsoft’s long-term commitment to defending Europe’s digital ecosystem—ensuring that, no matter how the threat landscape evolves, we will remain a trusted and steadfast partner to Europe in securing its digital future.
The need for new steps – the current threat environment
Microsoft continues to observe persistent threat activity targeting European networks from nation state actors, with Russian and Chinese activity being particularly prolific in Europe. Unsurprisingly, Russia continues to be especially focused on targets in Ukraine and European nations providing support to Ukraine. Nation-state actors, including those engaging in malicious activity from Iran and North Korea, are predominantly pursuing espionage objectives in Europe through credential theft or the exploitation of vulnerabilities to gain access to corporate and government networks. Several campaigns, including those from China, have also targeted academic institutions, compromising accounts to access sensitive research data or conduct geopolitical espionage against think tanks. Cybercriminals continue to develop Ransomware-as-a-Service beyond nation-state threats. We have seen the emergence of illicit websites rapidly gaining followings by leaking ransomware insights to be used by criminal groups to conduct attacks across Europe.
The rise of AI is also augmenting and evolving threat actor behavior. Microsoft has observed AI use by threat actors for reconnaissance, vulnerability research, translation, LLM-refined operational command techniques, resource development, scripting techniques, detection evasion, social engineering, and brute force attacks. This is why Microsoft now tracks any malicious use of new AI models we release and proactively prevents known threat actors from using our AI products. This also underscores the importance of secure development and rigorous testing of AI models, leveraging AI to benefit cyber defenders, and close public-private partnerships to share the latest insights about AI and cybersecurity.
Increasing AI-based threat intelligence sharing with governments
Microsoft’s Government Security Program (GSP) has long provided governments with confidential security information and resources to help them better understand our products and the evolving threat landscape, particularly threats from nation-state actors. Building on existing efforts, our new European Security Program will increase the flow and expand access to actionable threat intelligence to European governments. Tailored to discrete national threat environments using AI insights, and delivered, when possible, in real time, this program is designed to help governments stay ahead of advancing cyber threats through:
- Leveraging threat intelligence insights – Microsoft tracks the most sophisticated nation-state cyber activity, offering timely insights into evolving global threats. We use AI to support our analysis, which has improved our visibility and accelerated our ability to share the latest intelligence on the tactics, techniques, and procedures used by advanced persistent threat actors, including the malicious use of AI. By providing more information and faster, Microsoft will help European governments strengthen their cyber resilience and enable proactive defense.
- Expanding cybercrime reporting – The Microsoft Digital Crimes Unit (DCU) plays a critical role in detecting and disrupting global cybercriminal infrastructure, generating invaluable real-time intelligence in the process. As part of this new effort, we are expanding the availability of this intelligence to trusted European partners to support rapid response and coordinated enforcement action through the Cybercrime Threat Intelligence Program (CTIP).
- Providing foreign influence operations updates – The Microsoft Threat Analysis Center (MTAC) continues to monitor influence operations in Europe, which are increasingly using AI to mislead and deceive with deepfake synthetic media. MTAC also uses AI to look for commonalities across operations and will provide regular intelligence briefings on foreign influence, offering timely insights into the tactics, narratives, and digital platforms leveraged by state-affiliated actors. These briefings help policymakers and security stakeholders stay ahead of evolving disinformation campaigns and hybrid threats targeting democratic institutions and public trust.
- Identifying vulnerabilities and prioritizing security communications – Microsoft is committed to proactive and transparent security communications, particularly in the face of emerging threats and evolving vulnerabilities. We provide customers with timely, actionable intelligence through structured programs such as the Threat Microsoft Security Update Guide, Vulnerability Reporting process, and Microsoft Defender Vulnerability Management. As part of this expanded commitment, we will offer prioritized notice of security communications, including vulnerability remediation guidance to our European Security Program partners, helping to enhance situational awareness and enabling faster responses.
Participating governments will have a dedicated Microsoft point of contact to coordinate responses and escalate concerns. These efforts are designed to improve situational awareness and to support faster, more coordinated action across borders.
Making additional investments to strengthen cybersecurity capacity and resilience
Digital resilience—the ability to anticipate, withstand, recover from, and adapt to cyber threats and disruptions—requires more than technology. It requires investment in people, institutions, and partnerships. As part of the European Security Program, we are investing additional resources to further our work with European governments, civil society, and innovators to strengthen local capabilities and build long-term resilience. Highlights include:
- Strengthening public-private collaboration – Microsoft has launched a new pilot program with Europol’s European Cybercrime Centre (EC3), embedding Microsoft Digital Crimes Unit (DCU) investigators at EC3 headquarters in The Hague to enhance intelligence sharing and operational coordination. Through this enhanced collaboration, we will enable joint investigations, identify faster threat identification, and be better positioned to disrupt cybercriminal activity targeting European institutions and citizens more effectively.
- Supporting civil society and defending against ransomware – Microsoft has renewed our three-year partnership with the CyberPeace Institute to support NGOs and to promote accountability for bad actors, including nearly 100 Microsoft employees volunteering their time and expertise to help defend the most vulnerable in cyberspace. We will continue to support the Institute’s efforts to trace ransomware origins, identify safe havens, and uncover potential links to nation-state actors.
- Expanding cybersecurity support to the Western Balkans – Through a new collaboration with the Western Balkans Cyber Capacity Centre (WB3C), Microsoft will scale cybersecurity in a region where malicious actors have long sought to destabilize countries bordering the EU. Microsoft stands firmly in defense of Ukraine and is now extending that commitment with WB3C to help scale cybersecurity capabilities in a geopolitically sensitive and digitally under-resourced region, aligning with broader European cybersecurity priorities.
- Advancing AI security and innovation – Microsoft is investing additional resources to support research, expand the cybersecurity talent pipeline, and test advanced AI-assisted security tools in real-world environments using Microsoft’s security stack and Azure and Copilot capabilities. We’re working with the UK’s Laboratory for AI Security Research (LASR), a public-private partnership established to advance AI security in support of UK’s national security and economic prosperity. Together, we’re launching a joint research program focused on AI-cybersecurity challenges with a focus on critical infrastructure and agentic AI security, with an initial investment from Microsoft and research-collaboration between LASR and Microsoft Security Research Center.
- Securing open-source innovation – Through the recently launched GitHub Secure Open Source Fund, we will support open-source projects that underpin the digital supply chain, catalyze innovation, and are critical to the AI stack. By raising the security posture for European projects such as Log4J and Scancode, which are critical to the IT systems of governments and companies across the continent, the program aims to reduce future security vulnerabilities. Ensuring these tools can continuously withstand and sustainably defend against sophisticated cyber threats is essential to strengthening cyber resilience.
These new and enhanced initiatives reflect our belief that cybersecurity is a collective endeavor—and that Europe’s digital resilience must be built from the ground up.
Expanding partnerships to disrupt cyberattacks and dismantle cybercriminal networks
Finally, as part of our European Security Program we are expanding our partnerships with law enforcement and regional actors to proactively identify new and innovative ways to disrupt malicious and criminal activity.
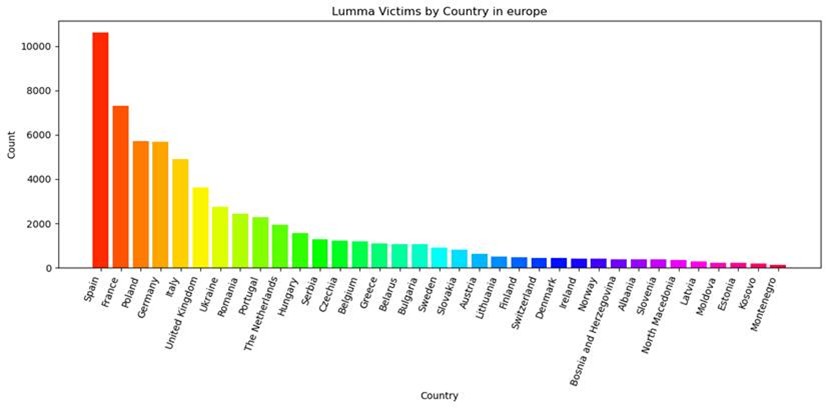
For instance, last month, Microsoft’s Digital Crimes Unit (DCU) worked with Europol and others to take down Lumma, a prolific infostealer malware used to steal passwords, financial data, and crypto wallets. In just two months, Lumma infected nearly 400,000 devices globally, many of them in Europe. The operation seized or blocked over 2,300 command-and-control domains. Off the back of this action, we are working with Europol to identify new opportunities to continue to meaningfully disrupt and deter cybercrime.
To accelerate future takedowns, we also launched the Statutory Automated Disruption (SAD) Program in April 2025. This initiative automates legal abuse notifications to hosting providers, enabling faster removal of malicious domains and IP addresses. Focused initially on Europe and the U.S., SAD raises the cost of doing business for cybercriminals and makes it harder for them to operate at scale.
In addition, we’re working with local internet service providers to help remediate affected users and ensure governments have greater visibility into emerging threats.
The DCU has long played a leading role in proactively combating cyber threats, including those originating from nation-state actors. Since 2016, Microsoft has filed seven legal actions to spotlight and disrupt nation-state threat actors from countries such as Russia, China, Iran, and North Korea, which we refer to internally by the weather-themed names Blizzard, Typhoon, Sandstorm, and Sleet, respectively. Most recently, in September 2024, Microsoft initiated a disruption action against the Russian actor Star Blizzard, mentioned above, known for hacking political targets surrounding UK’s 2022 elections and targeting NATO countries to advance its geopolitical interests involving Ukraine. Microsoft exposed the Russian actors and directly seized over 140 malicious domains in total, substantially blunting ongoing campaigns and forcing Star Blizzard to significantly alter its attack methods to other platforms, which Microsoft Threat Intelligence thereafter publicly exposed in a security blog. We will continue to act against those seeking to harm customers, governments, and individual users. These efforts are part of our broader strategy to partner with law enforcement across Europe. We are already working on coordinated disruptions to protect the digital ecosystem, and we stand ready to provide robust incident response services during crises, ensuring our partners and customers are never alone in the face of cyber adversity.
We also believe that deterrence is a critical pillar of modern cybersecurity. The EU’s Cyber Diplomacy Toolbox plays a vital role in this effort, helping to coordinate crisis response and send a clear message that malicious activity will not go unanswered—legally, operationally, or reputationally.
Taken together, operations like the Lumma disruption, the launch of SAD, and future coordinated disruptions are helping to prevent cybercriminals and state actors from establishing malicious infrastructure in Europe.
* * *
At Microsoft, our commitment to Europe is deep, enduring, and unwavering. We believe that Europe’s digital future is one of the most important opportunities of our time—and protecting that future is a responsibility we share. We will stand shoulder to shoulder with European governments, institutions, and communities to defend against threats, build capacity, and strengthen resilience. We are proud to be a trusted partner to Europe, and we will continue to work every day to earn trust through transparency, collaboration, and a steadfast commitment to protecting what matters most.
The post Microsoft launches new European Security Program appeared first on Microsoft On the Issues.
SVG animations take me back to the Hanna-Barbera cartoons I watched as a kid. Shows like Wacky Races, The Perils of Penelope Pitstop, and, of course, Yogi Bear. They inspired me to lovingly recreate some classic Toon Titles using CSS, SVG, and SMIL animations.
But getting animations to load quickly and work smoothly needs more than nostalgia. It takes clean design, lean code, and a process that makes complex SVGs easier to animate. Here’s how I do it.


Keeping things simple is key to making SVGs that are optimised and ready to animate. Tools like Adobe Illustrator convert bitmap images to vectors, but the output often contains too many extraneous groups, layers, and masks. Instead, I start cleaning in Sketch, work from a reference image, and use the Pen tool to create paths.
Tip: Affinity Designer (UK) and Sketch (Netherlands) are alternatives to Adobe Illustrator and Figma. Both are independent and based in Europe. Sketch has been my default design app since Adobe killed Fireworks.Beginning With Outlines
For these Toon Titles illustrations, I first use the Pen tool to draw black outlines with as few anchor points as possible. The more points a shape has, the bigger a file becomes, so simplifying paths and reducing the number of points makes an SVG much smaller, often with no discernible visual difference.

Bearing in mind that parts of this Yogi illustration will ultimately be animated, I keep outlines for this Bewitched Bear’s body, head, collar, and tie separate so that I can move them independently. The head might nod, the tie could flap, and, like in those classic cartoons, Yogi’s collar will hide the joins between them.

With the outlines in place, I use the Pen tool again to draw new shapes, which fill the areas with colour. These colours sit behind the outlines, so they don’t need to match them exactly. The fewer anchor points, the smaller the file size.

Sadly, neither Affinity Designer nor Sketch has tools that can simplify paths, but if you have it, using Adobe Illustrator can shave a few extra kilobytes off these background shapes.

It’s not just metadata that makes SVG bulkier. The way you export from your design app also affects file size.

Exporting just those simple background shapes from Adobe Illustrator includes unnecessary groups, masks, and bloated path data by default. Sketch’s code is barely any better, and there’s plenty of room for improvement, even in its SVGO Compressor code. I rely on Jake Archibald’s SVGOMG, which uses SVGO v3 and consistently delivers the best optimised SVGs.

My process for preparing SVGs for animation goes well beyond drawing vectors and optimising paths — it also includes how I structure the code itself. When every visual element is crammed into a single SVG file, even optimised code can be a nightmare to navigate. Locating a specific path or group often feels like searching for a needle in a haystack.

That’s why I develop my SVGs in layers, exporting and optimising one set of elements at a time — always in the order they’ll appear in the final file. This lets me build the master SVG gradually by pasting it in each cleaned-up section. For example, I start with backgrounds like this gradient and title graphic.

Instead of facing a wall of SVG code, I can now easily identify the background gradient’s path and its associated linearGradient, and see the group containing the title graphic. I take this opportunity to add a comment to the code, which will make editing and adding animations to it easier in the future:
<svg ...>
<defs>
<!-- ... -->
</defs>
<path fill="url(#grad)" d="…"/>
<!-- TITLE GRAPHIC -->
<g>
<path … />
<!-- ... -->
</g>
</svg>

Next, I add the blurred trail from Yogi’s airborne broom. This includes defining a Gaussian Blur filter and placing its path between the background and title layers:
<svg ...>
<defs>
<linearGradient id="grad" …>…</linearGradient>
<filter id="trail" …>…</filter>
</defs>
<!-- GRADIENT -->
<!-- TRAIL -->
<path filter="url(#trail)" …/>
<!-- TITLE GRAPHIC -->
</svg>

Then come the magical stars, added in the same sequential fashion:
<svg ...>
<!-- GRADIENT -->
<!-- TRAIL -->
<!-- STARS -->
<!-- TITLE GRAPHIC -->
</svg>
To keep everything organised and animation-ready, I create an empty group that will hold all the parts of Yogi:
<g id="yogi">...</g>

Then I build Yogi from the ground up — starting with background props, like his broom:
<g id="broom">...</g>
Followed by grouped elements for his body, head, collar, and tie:
<g id="yogi">
<g id="broom">…</g>
<g id="body">…</g>
<g id="head">…</g>
<g id="collar">…</g>
<g id="tie">…</g>
</g>

Since I export each layer from the same-sized artboard, I don’t need to worry about alignment or positioning issues later on — they’ll all slot into place automatically. I keep my code clean, readable, and ordered logically by layering elements this way. It also makes animating smoother, as each component is easier to identify.
Reusing Elements With<use>
When duplicate shapes get reused repeatedly, SVG files can get bulky fast. My recreation of the “Bewitched Bear” title card contains 80 stars in three sizes. Combining all those shapes into one optimised path would bring the file size down to 3KB. But I want to animate individual stars, which would almost double that to 5KB:
<g id="stars">
<path class="star-small" fill="#eae3da" d="..."/>
<path class="star-medium" fill="#eae3da" d="..."/>
<path class="star-large" fill="#eae3da" d="..."/>
<!-- ... -->
</g>
Moving the stars’ fill attribute values to their parent group reduces the overall weight a little:
<g id="stars" fill="#eae3da">
<path class="star-small" d="…"/>
<path class="star-medium" d="…"/>
<path class="star-large" d="…"/>
<!-- ... -->
</g>

But a more efficient and manageable option is to define each star size as a reusable template:
<defs>
<path id="star-large" fill="#eae3da" fill-rule="evenodd" d="…"/>
<path id="star-medium" fill="#eae3da" fill-rule="evenodd" d="…"/>
<path id="star-small" fill="#eae3da" fill-rule="evenodd" d="…"/>
</defs>
With this setup, changing a star’s design only means updating its template once, and every instance updates automatically. Then, I reference each one using <use> and position them with x and y attributes:
<g id="stars">
<!-- Large stars -->
<use href="#star-large" x="1575" y="495"/>
<!-- ... -->
<!-- Medium stars -->
<use href="#star-medium" x="1453" y="696"/>
<!-- ... -->
<!-- Small stars -->
<use href="#star-small" x="1287" y="741"/>
<!-- ... -->
</g>
This approach makes the SVG easier to manage, lighter to load, and faster to iterate on, especially when working with dozens of repeating elements. Best of all, it keeps the markup clean without compromising on flexibility or performance.
Adding AnimationsThe stars trailing behind Yogi’s stolen broom bring so much personality to the animation. I wanted them to sparkle in a seemingly random pattern against the dark blue background, so I started by defining a keyframe animation that cycles through different opacity levels:
@keyframes sparkle {
0%, 100% { opacity: .1; }
50% { opacity: 1; }
}
Next, I applied this looping animation to every use element inside my stars group:
#stars use {
animation: sparkle 10s ease-in-out infinite;
}
The secret to creating a convincing twinkle lies in variation. I staggered animation delays and durations across the stars using nth-child selectors, starting with the quickest and most frequent sparkle effects:
/* Fast, frequent */
#stars use:nth-child(n + 1):nth-child(-n + 10) {
animation-delay: .1s;
animation-duration: 2s;
}
From there, I layered in additional timings to mix things up. Some stars sparkle slowly and dramatically, others more randomly, with a variety of rhythms and pauses:
/* Medium */
#stars use:nth-child(n + 11):nth-child(-n + 20) { ... }
/* Slow, dramatic */
#stars use:nth-child(n + 21):nth-child(-n + 30) { ... }
/* Random */
#stars use:nth-child(3n + 2) { ... }
/* Alternating */
#stars use:nth-child(4n + 1) { ... }
/* Scattered */
#stars use:nth-child(n + 31) { ... }
By thoughtfully structuring the SVG and reusing elements, I can build complex-looking animations without bloated code, making even a simple effect like changing opacity sparkle.

Then, for added realism, I make Yogi’s head wobble:
@keyframes headWobble {
0% { transform: rotate(-0.8deg) translateY(-0.5px); }
100% { transform: rotate(0.9deg) translateY(0.3px); }
}
#head {
animation: headWobble 0.8s cubic-bezier(0.5, 0.15, 0.5, 0.85) infinite alternate;
}
His tie waves:
@keyframes tieWave {
0%, 100% { transform: rotateZ(-4deg) rotateY(15deg) scaleX(0.96); }
33% { transform: rotateZ(5deg) rotateY(-10deg) scaleX(1.05); }
66% { transform: rotateZ(-2deg) rotateY(5deg) scaleX(0.98); }
}
#tie {
transform-style: preserve-3d;
animation: tieWave 10s cubic-bezier(0.68, -0.55, 0.27, 1.55) infinite;
}
His broom swings:
@keyframes broomSwing {
0%, 20% { transform: rotate(-5deg); }
30% { transform: rotate(-4deg); }
50%, 70% { transform: rotate(5deg); }
80% { transform: rotate(4deg); }
100% { transform: rotate(-5deg); }
}
#broom {
animation: broomSwing 4s cubic-bezier(0.5, 0.05, 0.5, 0.95) infinite;
}
And, finally, Yogi himself gently rotates as he flies on his magical broom:
@keyframes yogiWobble {
0% { transform: rotate(-2.8deg) translateY(-0.8px) scale(0.998); }
30% { transform: rotate(1.5deg) translateY(0.3px); }
100% { transform: rotate(3.2deg) translateY(1.2px) scale(1.002); }
}
#yogi {
animation: yogiWobble 3.5s cubic-bezier(.37, .14, .3, .86) infinite alternate;
}
All these subtle movements bring Yogi to life. By developing structured SVGs, I can create animations that feel full of character without writing a single line of JavaScript.
Try this yourself:
See the Pen Bewitched Bear CSS/SVG animation [forked] by Andy Clarke.
ConclusionWhether you’re recreating a classic title card or animating icons for an interface, the principles are the same:
- Start clean,
- Optimise early, and
- Structure everything with animation in mind.
SVGs offer incredible creative freedom, but only if kept lean and manageable. When you plan your process like a production cell — layer by layer, element by element — you’ll spend less time untangling code and more time bringing your work to life.

James sits down with Eric Sink who created and maintains SQLitePCLRaw, which is the foundation of just about everything SQLite for .NET developers. We discuss what it is, how developers actually use it, it's future, and how to contribute.
✅ Chapters:
00:00 - Introduction
00:30 - What is SQLitePCL.raw
06:00 - Working with SQLitePCL.raw directly
11:40 - Open source & supporting the project
19:00 - Wrap-up
✅ Resources:
SourceGear & SQLite services: https://services.sourcegear.com/
SQLitePCL.raw on GitHub: https://github.com/ericsink/SQLitePCL.raw
NuGet: https://www.nuget.org/packages/sqlitepclraw.core/
SQLite Forums: https://sqlite.org/forum/forum
Connect with .NET:
Blog: https://aka.ms/dotnet/blog
Twitter: https://aka.ms/dotnet/twitter
TikTok: https://aka.ms/dotnet/tiktok
Mastodon: https://aka.ms/dotnet/mastodon
LinkedIn: https://aka.ms/dotnet/linkedin
Facebook: https://aka.ms/dotnet/facebook
Docs: https://learn.microsoft.com/dotnet
Forums: https://aka.ms/dotnet/forums
🙋♀️Q&A: https://aka.ms/dotnet-qa
👨🎓Microsoft Learn: https://aka.ms/learndotnet
#dotnet
Joel Bancroft-Connors: The 90-Day Rule—Building Trust Before Disrupting the Status Quo
Read the full Show Notes and search through the world's largest audio library on Agile and Scrum directly on the Scrum Master Toolbox Podcast website: http://bit.ly/SMTP_ShowNotes.
Joel shares his first experience as a CSM at a traditional hard drive manufacturing company, where he learned the art of patient change management. Tasked with bridging the gap between a rigid mothership company and their agile startup division, Joel discovered the power of focusing on principles rather than processes. For six months, he concentrated on creating transparency and shifting focus from status reporting to "getting to done" without ever mentioning Scrum or Agile.
His approach followed what he calls the 90-day rule: "In the first 90 days - do no harm, but then have a plan to do something." By listening first and building trust, Joel helped the team deliver a product in just three months. He emphasizes the importance of making people feel valued and using "future perfect thinking" to envision desired outcomes before introducing change.
In this episode we refer to Luke Hohmann’s Innovation Games, the website and resource Manager-Tools.com, and Daniel Pink’s book Drive.
Self-reflection Question: Are you rushing to implement changes, or are you taking time to build trust and understand the current state before introducing new practices?
[Scrum Master Toolbox Podcast Recommends]
🚀 Global Agile Summit 2025
Join us in Tallinn, Estonia, from May 18th – 20th, 2025, for an event that will inspire, challenge, and equip you with real-world Agile success stories.
🌍 Connect with global Agile leaders.
💡 Learn practical strategies for impact.
🔥 Break free from Agile fatigue and become a Pragmatic Innovator
[Scrum Master Toolbox Podcast Recommends]
About Joel Bancroft-Connors
Joel Bancroft-Connors is The Gorilla Coach — a Certified Scrum Trainer and Agile disruptor focused on sustainable value and effectiveness. With a background in product, project, and coaching, Joel blends sharp insights with practical tools to help teams thrive. He is a Miro power user and rocks curated classroom playlists.
You can link with Joel Bancroft-Connors on LinkedIn.
Download audio: https://traffic.libsyn.com/secure/scrummastertoolbox/20250604_Joel_BC_W.mp3?dest-id=246429